Sophos UTM and Cisco IOS IPsec VPN
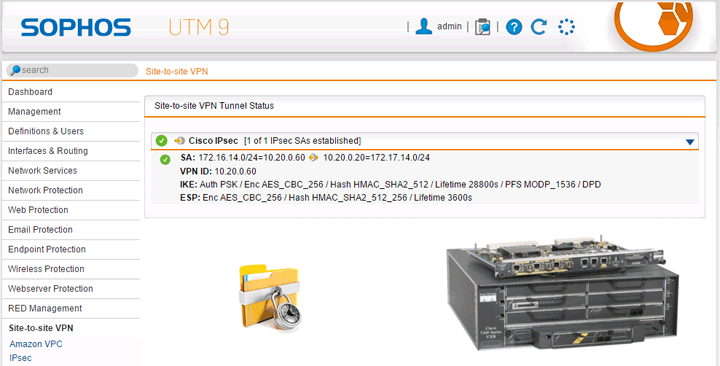
Today I’ll discuss doing a simple IPsec site-to-site VPN tunnel between a Sophos UTM and an IOS based Cisco 7200VXR series router. This example will be using Sophos UTM 9.3 and Cisco IOS 15 with the adventerprisek9 image.
Here’s the related running configuration of the Cisco router’s VPN settings:
access-list 101 permit ip 172.17.14.0 0.0.0.255 172.16.14.0 0.0.0.255 crypto isakmp policy 5 encr aes 256 hash sha512 authentication pre-share group 5 lifetime 28800 crypto isakmp key mysecretkey address 10.20.0.60 crypto ipsec transform-set SophosUTM esp-aes 256 esp-sha512-hmac crypto map SophosUTM 5 ipsec-isakmp set peer 10.20.0.60 set transform-set SophosUTM set pfs group5 match address 101 interface FastEthernet0/0 crypto map SophosUTM
The above reflects the Cisco’s local network as 172.17.14.0/24 and the remote network as 172.16.14.0/24. The Phase I/II encryption is set to AES 256 and SHA512 using a pre-shared key. IKE DH group is set to 5, and PFS is also enabled with DH group 5. The IKE SA lifetime has been set to 28800 and IPsec SA lifetime set to 3600. The Sophos UTM and Cisco router are both on the 10.20.0.0/24 network with FastEthernet0/0 having the 10.20.0.20 IP. Now let’s configure the Sophos UTM side of the tunnel.
Step 1 – Create your policy
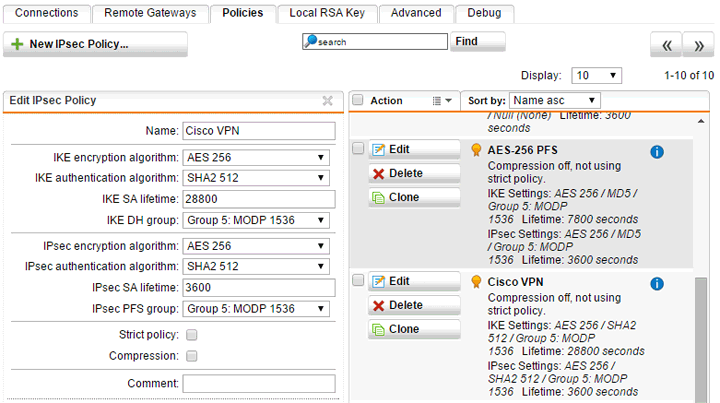
This part is pretty straight-forward. Simply select all of the same options for your Phase I/II settings as the Cisco configuration, and give your policy a relevant name.
Step 2 – Remote Gateway
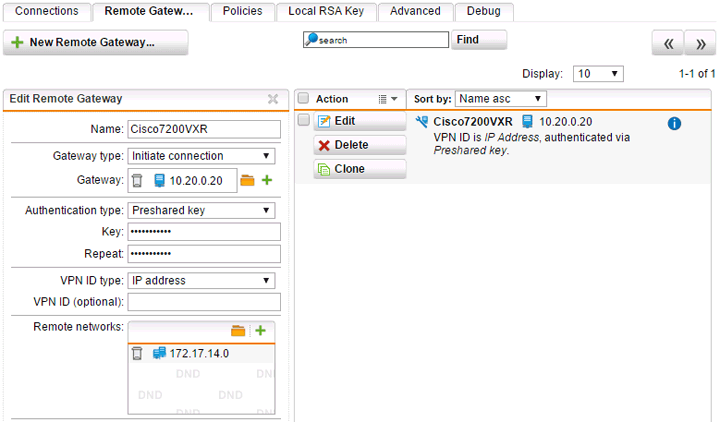
Create a new remote gateway with a descriptive name. Since our Cisco router’s IP isn’t subject to change, we can keep the type as “Initiate connection” instead of using “Respond only.” Enter the IP address of the remote gateway as a network object and enter your pre-shared key. You’ll also need to create a network object defining 172.17.14.0/24 as the remote network.
Step 3 – Create the connection
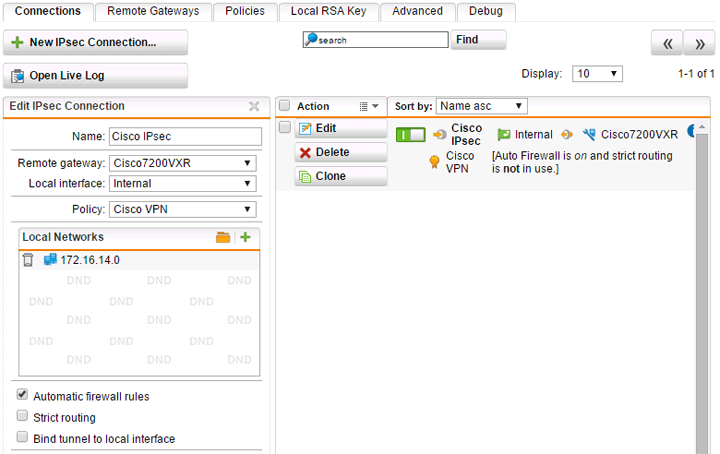
Seen above, select the remote gateway and policy you created in the earlier steps. The IP address 10.20.0.60 for this example is attached to the “Internal” interface on our Sophos UTM. In most cases you’d be using your external interface for VPN tunnels. If you don’t already have a network object created for your local network you’ll need to also add that.
Does it work?
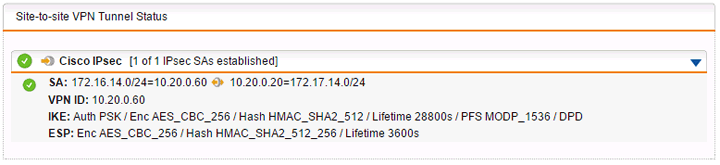
Everything seems to check out on the Sophos UTM side. Now let’s verify on the Cisco side.
C7200VXR# sh crypto session Crypto session current status Interface: FastEthernet0/0 Session status: UP-ACTIVE Peer: 10.20.0.60 port 500 IKEv1 SA: local 10.20.0.20/500 remote 10.20.0.60/500 Active IPSEC FLOW: permit ip 172.17.14.0/255.255.255.0 172.16.14.0/255.255.255.0 Active SAs: 2, origin: crypto map
You can also run sh crypto sa for much more detailed information.






1 Response
[…] Source : Sophos UTM and Cisco IOS IPsec VPN – OMGWTFBBQ! […]